Overview
Transform your development team with the REFLEX methodology - an evolutionary approach to embedding security into your software engineering DNA. Created by Java Champion Steve Poole, REFLEX helps teams stop reacting and start defending.
Transform your development team with the REFLEX methodology - an evolutionary approach to embedding security into your software engineering DNA. Created by Java Champion Steve Poole, REFLEX helps teams stop reacting and start defending.

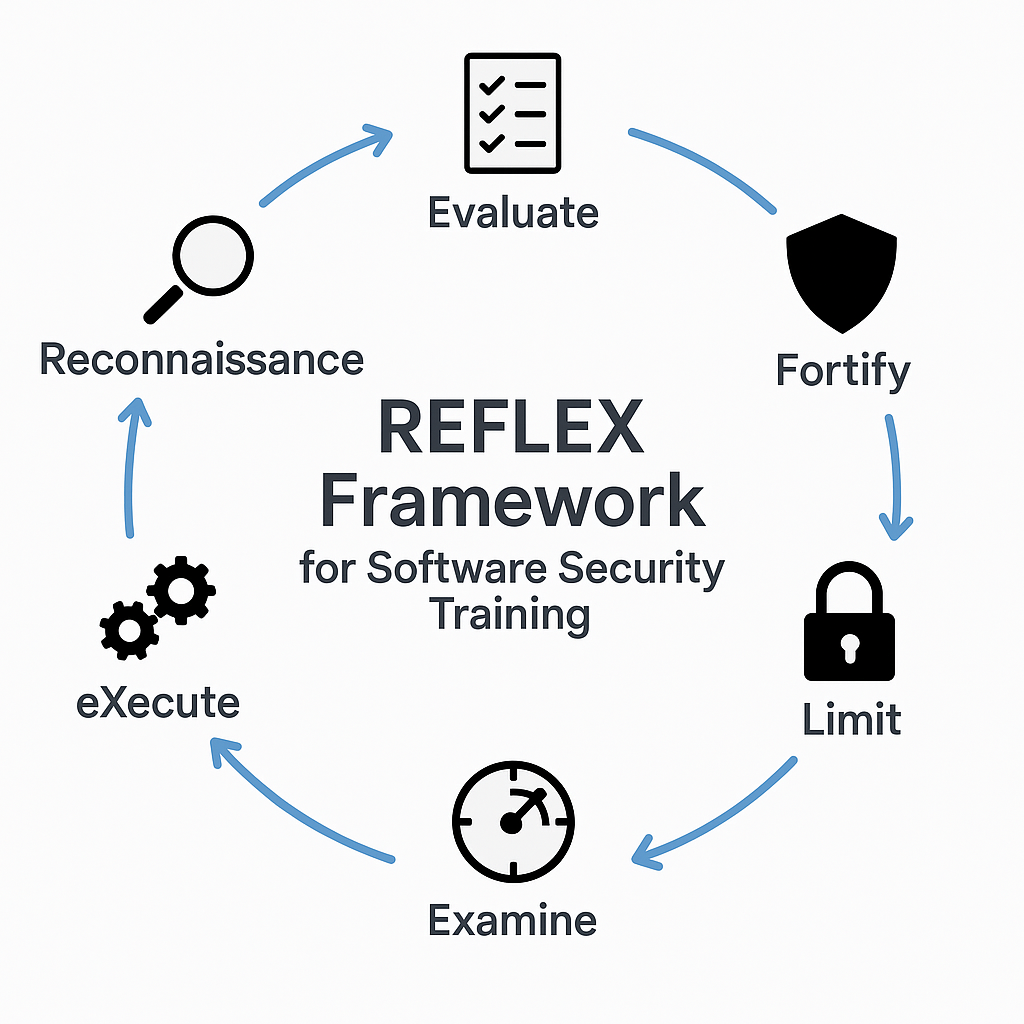
| Reconnaissance | Stay informed on vulnerabilities, AI risks, and external factors like regulations and cyberattack motivations. |
| Evaluate | Assess your environment and decisions from an attacker’s perspective to identify potential vulnerabilities. |
| Fortify | Build secure systems from the ground up by embedding security in design patterns, dependencies, and compliance. |
| Limit | Implement measures to limit the impact of attacks, such as isolation, encryption, and fail-safe mechanisms. |
| Examine | Detect and monitor unusual behaviors, compromised dependencies, and threats in real-time using logging and telemetry. |
| eXecute | Continuously refine and improve security practices through ongoing learning, post-incident reviews, and team collaboration. |